A study regarding the effectiveness of game play as part of an information security awareness program for novices | Semantic Scholar

Varonis: Fighting A Different Battle Than Traditional Cybersecurity Companies (NASDAQ:VRNS) | Seeking Alpha

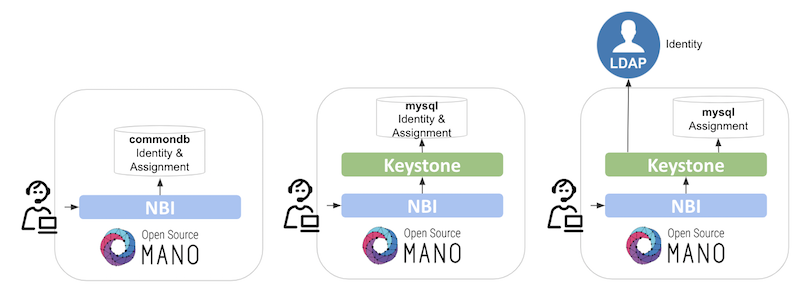
How do we secure ManoMano applications with our DIY pipeline ? | by Laurent Delosieres | ManoMano Tech Team | Medium