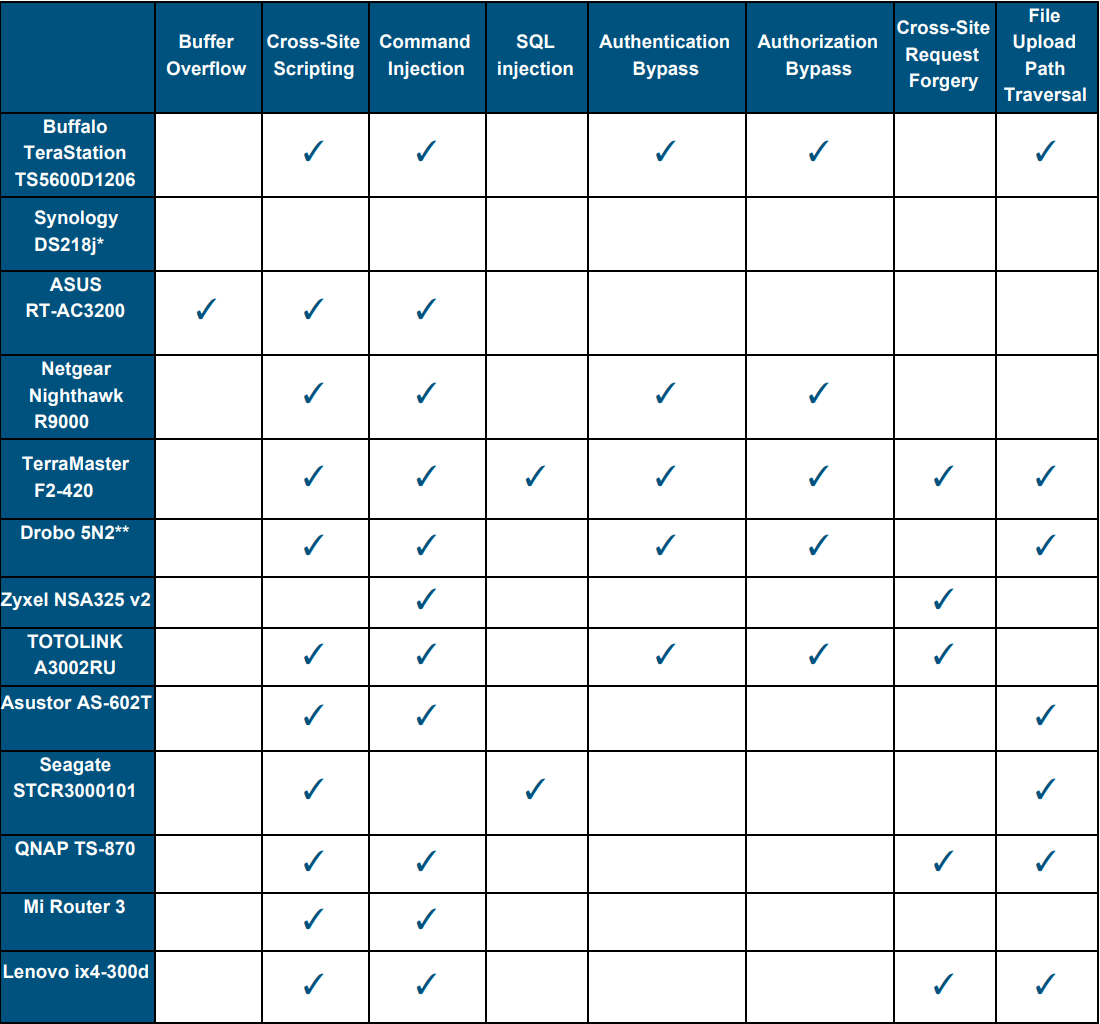
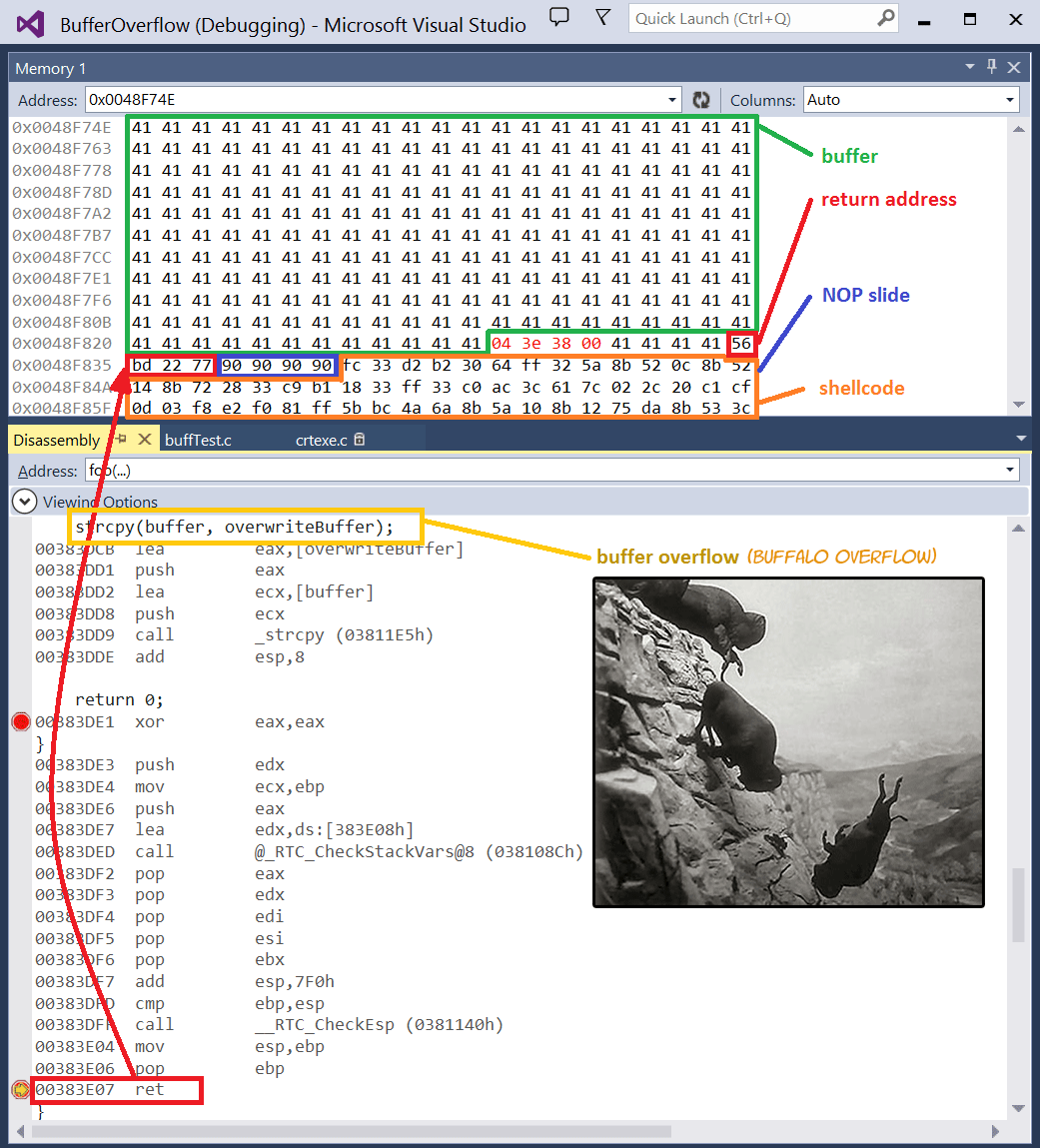
Matthew Hall on Twitter: "Also... not really “full stack” if memory corruption vulns aren't considered at all... some may say “yeah but when was the last time you found a buffer overflow

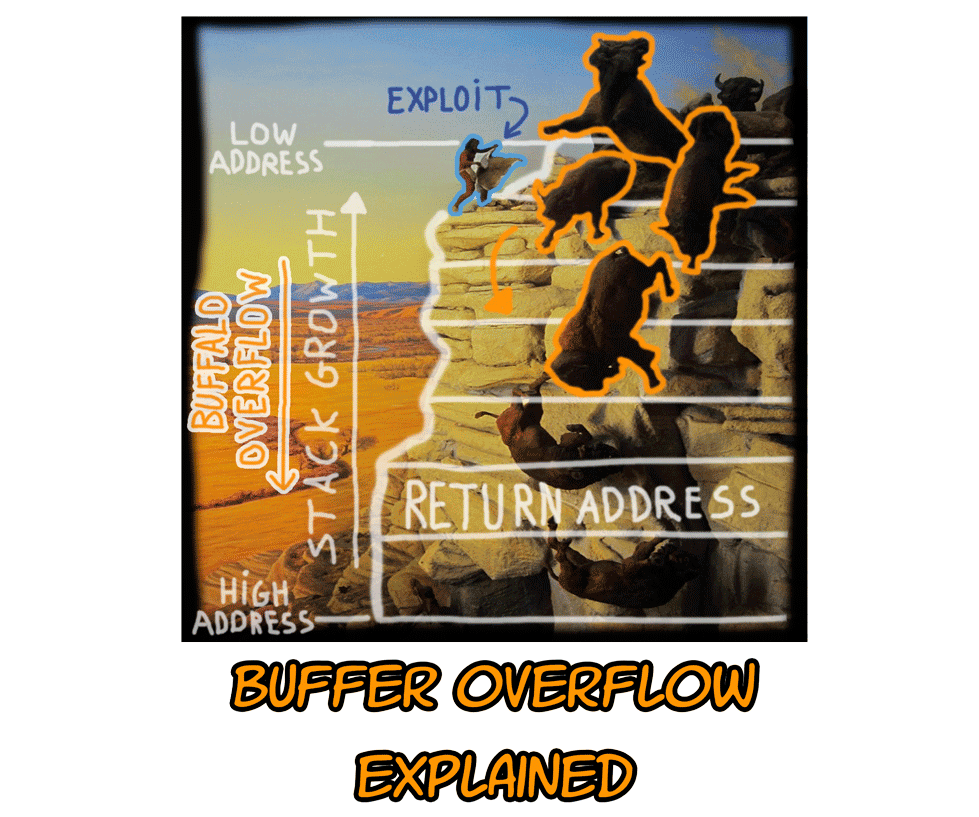
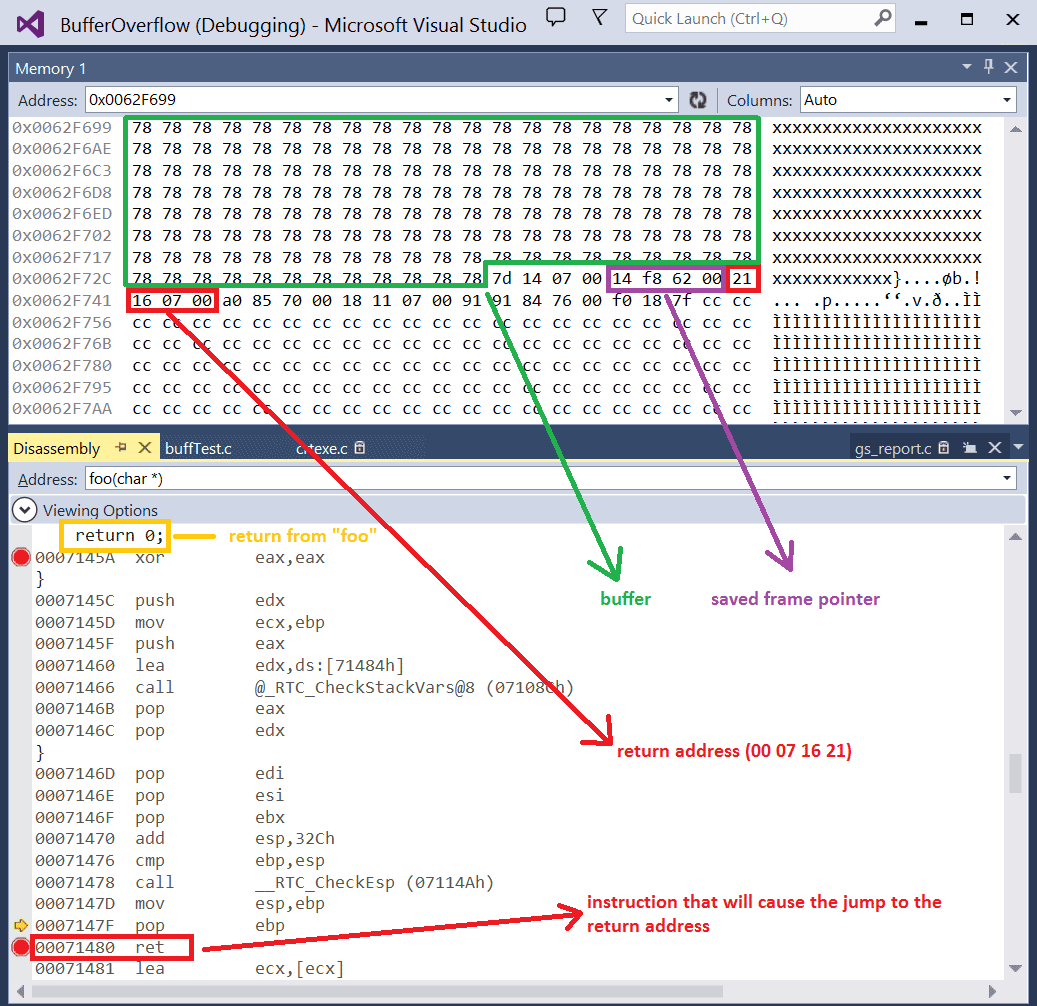
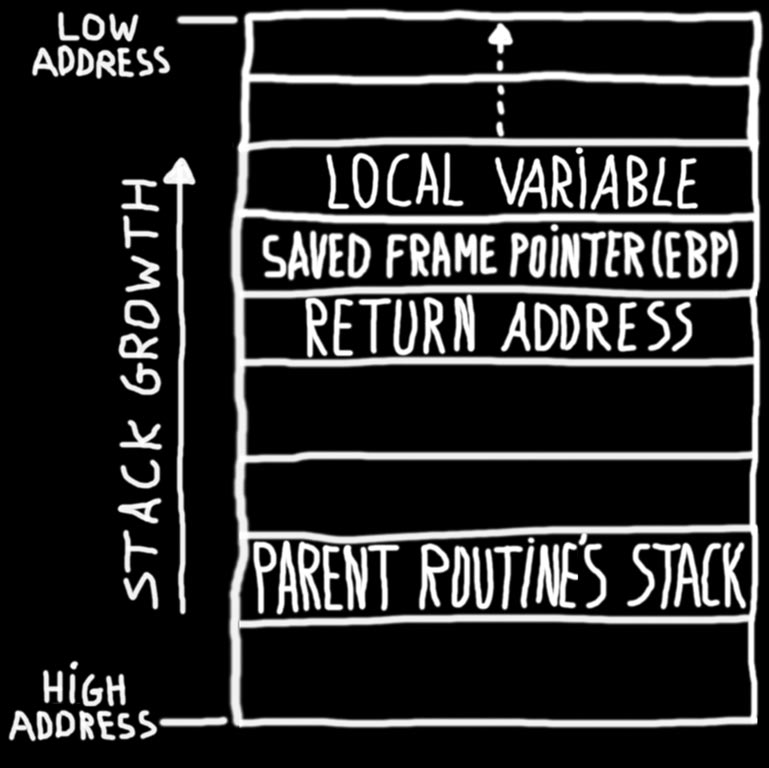
An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs

An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs